S Lab
[Sibin Mohan]
Systems Security Research Group at GWU and University of Illinois

Integrating Security as a First Class Principle in Real-Time Systems
Team Members: Sibin Mohan, Monowar Hasan
Collaborators: Rakesh Bobba, Rodolfo Pellizzoni
Embedded devices with real-time properties (e.g., strict timing and safety requirements) require interaction between cyber and physical worlds. These devices are used to monitor and control physical systems and processes in many domains, e.g., critical infrastructures like the electric grid, oil and gas pipelines, water systems, EDS control networks, process control systems in industrial plants, unmanned aerial vehicles (UAVs), submarines, electric vehicles to name just a few.

*Image courtesy: Krypt3ia
Given the drive towards remote monitoring and control, these devices are being increasingly interconnected, often via the Internet. Since many of these systems have to meet stringent safety and timing requirements, any problems that deter from the normal operation of such systems could result in damage to the system, the environment or pose a threat to human safety. Similar problems can occur if such systems are the target of malicious security attacks – a very valid concern since breaches are not uncommon in critical applications, especially considering the recent spate of IoT-centric attacks.
Enabling security in real-time systems (RTS) is often more challenging than generic enterprise systems due to additional real-time requirements (such as limited energy, safety and timing constraints). Stringent timing constraints in RTS introduce complexities – the strict deadlines for the real-time tasks may not allow for frequent execution of security mechanisms. For example, how often and how long should a monitoring and detection task execution to be effective but not interfere with real-time control or other safety-critical tasks? While this issue potentially be addressed for newer systems at design time, this is especially challenging for retrofitting legacy/existing systems where the real-time/control tasks are already in place and perhaps cannot be modified.
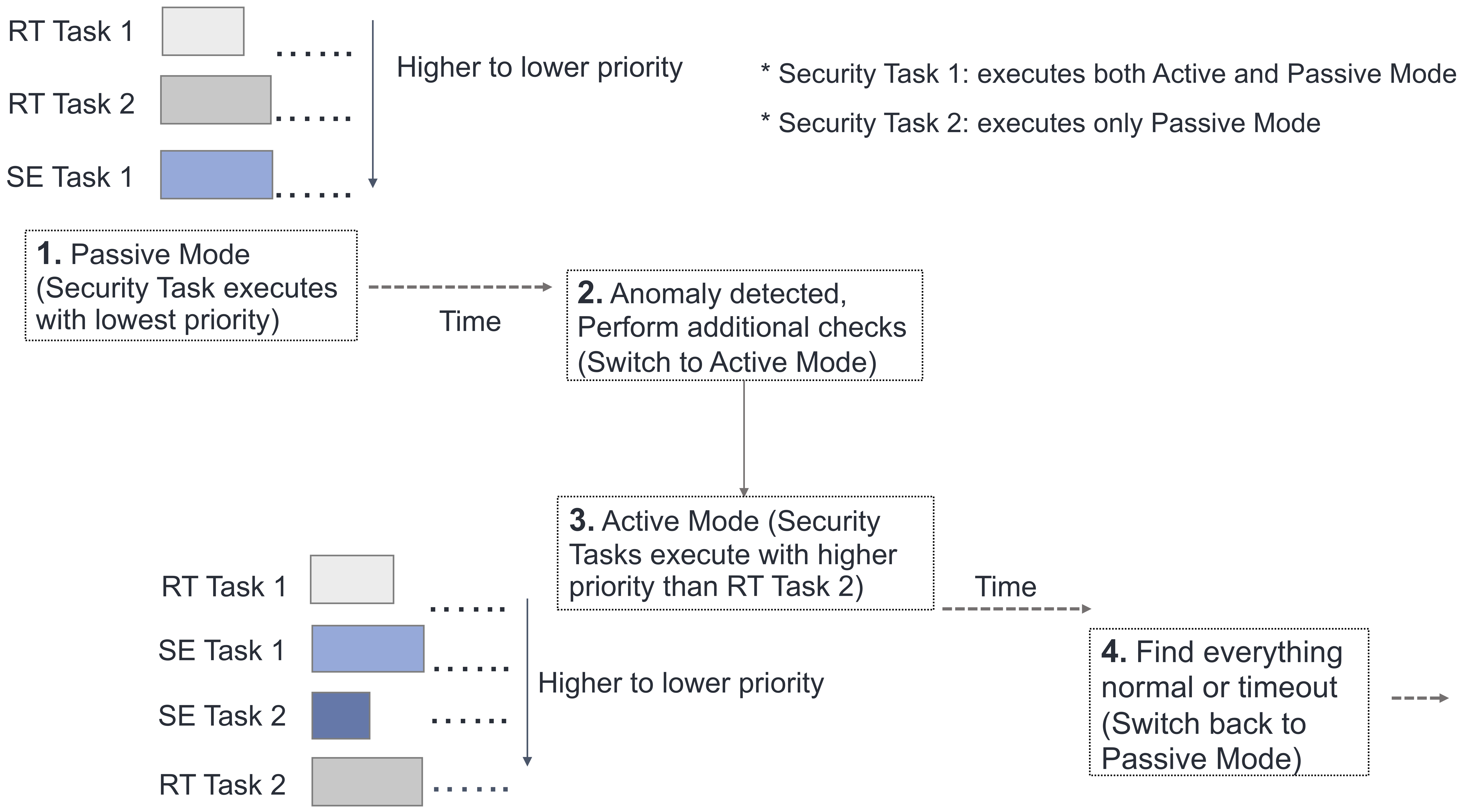
Illustration of an adaptive security integration mechanism: by default security tasks (say a given set of intrusion detection policies) execute with lowest priority (e.g., as a background process) – once any anomalous behavior is detected, the tasks get higher priority and perform more fined-grained system-wide checking.
The major focus of this project is to address the following:
how do we integrate and then characterize the effects of security in legacy time/safety critical systems (those designed using both single and multicore chips)?
Funding
- This project was initially funded by the Office of Naval Research (ONR).
Related Publications:
For legacy/existing systems
-
M. Hasan, S. Mohan, R. Pellizzoni, and R. Bobba, “A design-space exploration for allocating security tasks in multicore real-time systems,” in Proc. of Design, Automation and Test in Europe (DATE), pp. 225-230, Mar. 2018.
-
M. Hasan, S. Mohan, R. Pellizzoni, and R. Bobba, “Contego: An adaptive framework for integrating security tasks in real-time systems,” in Proc. of Euromicro Conference on Real-Time Systems (ECRTS), vol. 76, pp. 23:1-23:22, Jun. 2017.
-
M. Hasan, S. Mohan, R. Bobba, and R. Pellizzoni, “A server model to integrate security tasks into fixed-priority real-time systems,” in Proc. of Workshop on Security and Dependability of Critical Embedded Real-Time Systems (CERTS), pp. 61-68, Nov. 2016.
-
M. Hasan, S. Mohan, R. Bobba, and R. Pellizzoni, “Exploring opportunistic execution for integrating security into legacy hard real-time systems,” in Proc. of IEEE Real-Time Systems Symposium (RTSS), pp. 123-134, Nov. 2016.
Future systems
-
R. Pellizzoni, N. Paryab, M. K.Yoon, S. Bak, S. Mohan and R. Bobba. “A Generalized Model for Preventing Information Leakage in Hard Real-Time Systems”, in Proc. of IEEE conference in Real-Time and Embedded Systems and Applications Symposium (RTAS), April 2015.
-
S. Mohan, M. K. Yoon, R. Pellizzoni and R. Bobba., “Real-Time Systems Security Through Scheduler Constraints”, in Proc. of EUROMICRO Conference in Real-Time Systems (ECRTS), July 2014.
-
S. Mohan, M. K. Yoon, R. Pellizzoni and R. Bobba., “Integrating Security Constraints into Fixed Priority Real-Time Schedulers”, Real-Time Systems (RTS) Journal 52(5): 644-674.