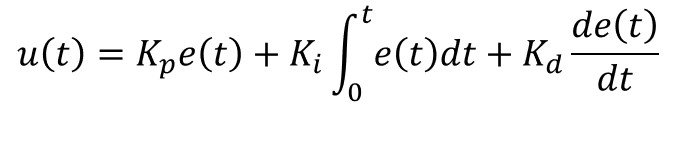Secure Autonomous Systems
Instructor: Prof. Sibin Mohan, The George Washington University
CSCI 6907/3907 | Fall 2022 | TR 12:45PM - 02:00PM PT | SMTH 115
MP IV: Rover control and attack
Administrivia
| Announcement Date |
Nov. 12, 2022 |
| Final Demo Date |
Dec. 9, 2022 |
| Submission Date |
Dec. 14, 2022 |
| Submission Time |
11:59PM |
| Total Points |
40 |
Objective
In this MP, we want to see what an adversary can do when it has access to the rover.
The assumption is the adversary gained privileged access to the rovers system by some method like brute forcing or a man-in-the-middle attack.
1. Make a new mission
1-A What is a waypoint?
Waypoints define the route that the robot follows. Each waypoint stores a position, and the robot tries to reach that point with its limitations.
For a new mission, you have to generate a new waypoint to show the rover the path it has to take. You can break a route into several points but how to choose them is important.
1-B Sampling the trajectory
Let's say we have a linear trajectory. The robot should go from (0,0) to (0,1). For this case, we can put infinite number of points between these two points, which doesn't make sense, while we can make the trajectory just
by using these 2 points; on the other hand, let's say we have a curve we need at least 3 points to sample that trajectory. For example, (0,0),(1,0),(0,1), we can add more points on that trajectory to help the rover to follow it better.
But sometimes, adding more waypoints will harm the system. What if waypoints are not put in correct sequence, or they are so close to each other that the rover will get stuck in waypoint changing state?
The question is can the rover reach each point in the correct sequence?
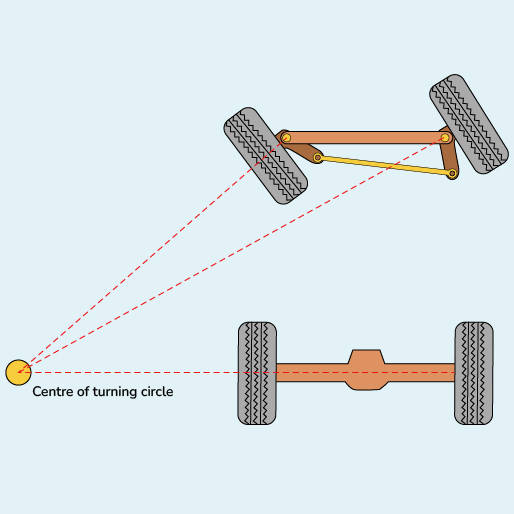
1-C Ackermann Steering
This is the mechanism used in cars where the front wheels are turning to control the steering of the vehicle. Rather than the differential robots, the Ackermann cannot reach all the points because it has a limit
on the steering. Our rover uses the same steering system.
1-D Rover
The waypoints file is located at catkin_ws/src/gwurover/src/trajectory. Each line is coordinated in order of "y,x,z". You have to edit the MP.csv file for the first part of this MP to make the shown trajectory in the submission part.
Each line shows a position, and the robot will automatically switch to another position(next line) after it reaches the point with an acceptable error.
To test the trajectory put the SG key on the radio controller in the middle state and pull the SF key up to start the mission.
2. Controller attack
A control system is a system that provides the desired response by controlling the output.
2-A PID controller
A proportional-integration-derivative PID controller is a system to control different operations like speed, flow rate, pressure, temperature, and various other processing variables. It provides the ability to automatically maintain the set value and compensate for changes in process and environment.
PID controller uses a closed feedback control system that regulates the required parameters to its set point/desired value by playing with various operations.
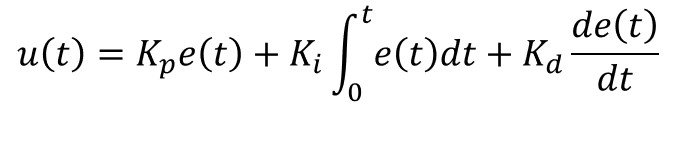
Kp, Ki, and Kd are proportional, integral, and deviation coefficients. These coefficients can also be represented as P, I, and D.
Tuning is the process of setting the optimal gains for Kp, Ki, and Kd to get an ideal response from a control system.
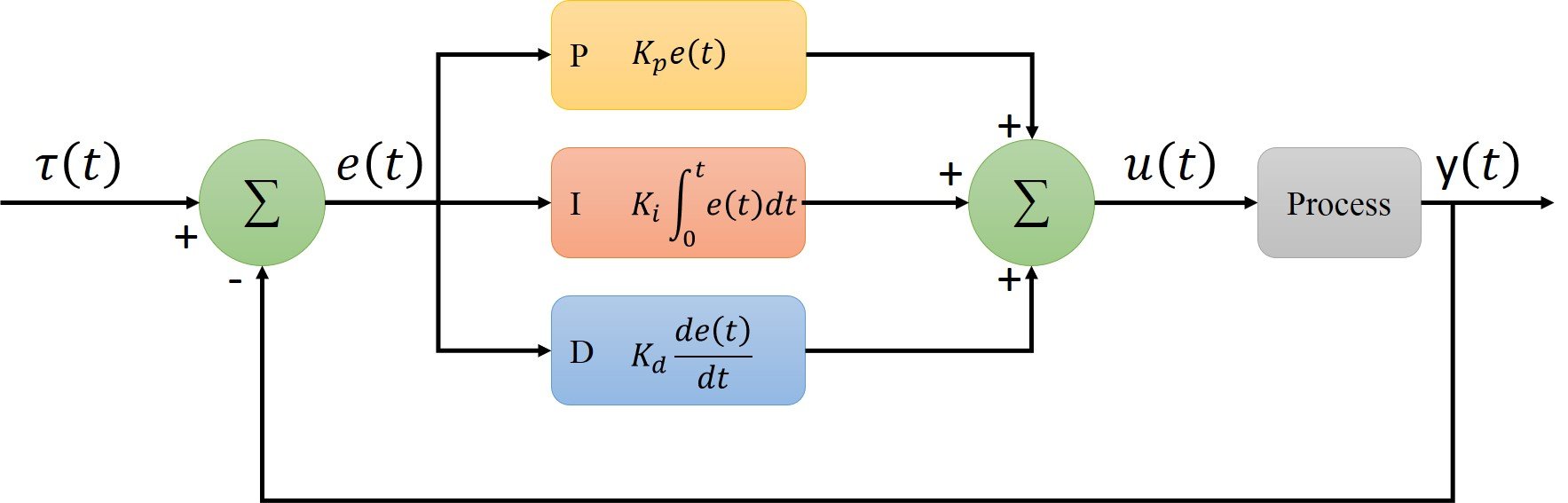
Two PID controllers control the position of the rover. The first one controls the speed, the other controls the steering angle, and
each PID controller has its coefficients, which are tuned.
For this Part, we want to play around with the coefficients and see how we can prevent the robot from following the correct orders.
When running ROS on the rover, there is a node listening(subscribing) on topic controller/pid_params, which can change the coefficients on the run. This is for further tunning the rover in a test.
Somehow the engineers forgot to encrypt or remove this access to the controller.
2-B How to publish data on a ROS topic
There are several ways to publish data on a certain topic. You can write a script in python or cpp to do that
but for this case, you can just use the terminal to publish the data just once, which you do with the following command:
rostopic pub <topic-name> <topic-type> [data...]
To find the topic type, you can run this command:
rostopic info <topic-name>
And finally, for the data structure, you can just tap the [tab] key twice, and the terminal will write the structure for you.
3. Timing attack
Timing attack covers a large part of definitions as a method to break the security mechanisms of an application by gaining information that is indirectly leaked by the application
form the time an algorithm takes. The other definition for this type of attack is to push a system to miss all the scheduled trimming. Generally, any attack related to time is called a timing attack.
3-A System scheduler
Scheduling is the process of controlling and prioritizing messages sent to a processor.
An internal operating system program called the scheduler performs this task.
The goal is to maintain a constant amount of work for the processor, eliminating highs and lows
in the workload and ensuring each process is completed within a reasonable time frame.
While scheduling is vital to all systems, it is crucial in real time.
Any process in the scheduler has a deadline which is a fundamental property in real-time systems like this rover.
The task should be done before the deadline. But what if the adversary can do something to occupy the whole processor's resources and push
the system to miss all deadlines?
The question you have to solve here is how to occupy all the rover's computational resources while running a mission.
Submission Instructions
-
Generate a mission: generating the path of the picture below by creating waypoints that the robot can take. To make the curve given in the below figure, the minimum number of waypoints you have to use is 3. [10 points]
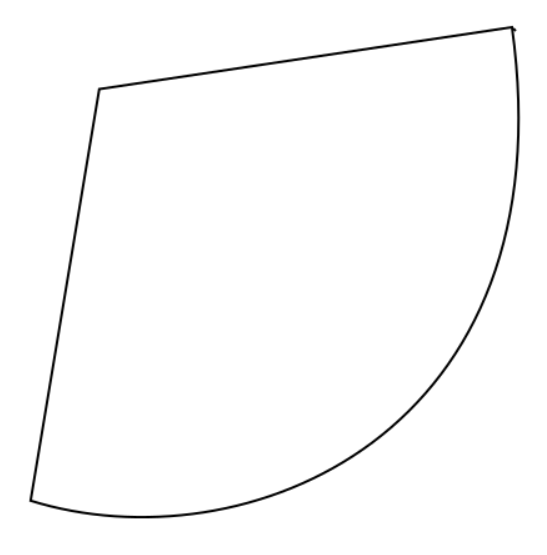
-
Controller attack: deploy the controller attack and make the rover stop middle of the mission, and show the result to TA. [15 points]
-
Timing attack: run the timing attack on all the missions you have (rectangle, eight, part1) and show the result to the TA. [15 points]
-
The group will submit a single one page document that clearly lists the contributions of each group member. This is one document per group.
-
Bonus:
Mathematically show that all the points you used to make the figure (In the 1st Submission) are reachable by rover. (You can use this paper for the calculation and reference.) [5 points]
-
Bonus:
Make the robot follow another path just by changing PID parameters. [5 points]
Final Demo
We will have the final demo for all the projects on Dec 9, 2022 (time and location will be announced soon).
- Each group will be assigned a time slot (e.g. 15 mins)
- The group is expected to demonstrate the mission generation, controller attack and timing attack during the demo.
- The group is also expected to present their approach and solution (a short presentation of 10 mins) during the demo.
Note: the final submission date is after the demo date (Dec. 14, 2022) but the grade is dependant on the demo and presentation. The extra days are just padding in case of minor glitches. You must demonstrate full working solutions on the Demo day!