omnetpp.ini files residing in the scenario directories.
We will again modify this file as first thing to set up attacks and some additional loggings. Go to Desktop/v2x_simulator/F2MD/F2MD/veins-f2md/f2md-networks/IRTSystemXScenario/omnetpp.ini
in your favorite text editor and make the following changes:
- Change the simulation length
sim-time-limitto1200sfor a 20 minute simulation: -
appl.MixLocalAttacks = trueto use a mix of all attack types in the list. -
appl.LOCAL_ATTACKER_PROB = 0.3to set 30% of all vehicles as attackers. - Set
appl.writeVeremi = trueto have all vehicles record their received message logs seperately to f2md-results file. - Set
appl.writeBSMsV1 = trueto record MBD BSM logs. - Set
appl.writeListBSMsV1 = trueto record aggregated MBD BSM logs. - Set
appl.writeReportsV1 = trueto record MBD reports by vehicles. - Set
appl.writeListReportsV1 = trueto record aggregated MBD BSM logs. -
Set
appl.EnableV1 = trueto enable V1 app socket of our misbehavior detection app to listen to simulation messages. -
Set
appl.SaveStatsV1 = trueto record MBD app logs. -
Set
appl.appTypeV1 = 0which is the simple thresholding MBD application. It essentially checks the message plausibilities and marks message as attacks plausibility score falls below certain threshold. -
Set
appl.checksVersionV1 = 0which is the simple legacy plausibility calculations. Essentially, these checks calculate certain plausibility measures for each message and adding 0 or 1, depending on if the message seems plausible or malicious.
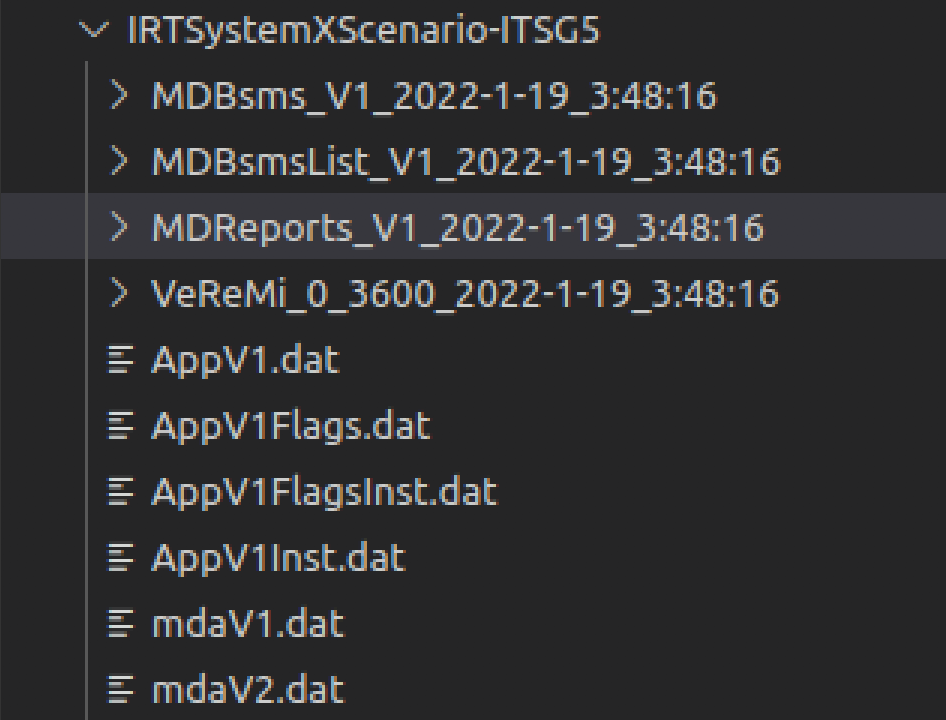
-
MDBSMs_V1: This is the seperate and timed records of all BSMs over the simulation, received by the Misbehaivor App. For instance, as the naming convention,MDBSM_V1_8-7028_10218_1090file refers to BSM records sent at t= 8.7028 seconds sent by vehicle with pseudonym ID 1090 and received by vehicle with pseudonym ID 10218. Pseudonym is a temporary certificate that vehicle uses as ID, and mapping from real IDs to pseudonyms are avaiable in all logs. -
MDBSMsList: This is the records of all BSMs over the simulation, received by the Misbehaivor App, per vheicle pseudonym. It is essentially an aggregated version of records at (a). For instance, as the naming convention,MDBSM_V1_1090file refers to BSM records received by vehicle with pseudonym ID 1090 during simulation. -
MDReports: This is the collective misbehavior reports generated by our detection app. For instance, as the naming convention,MDReport_V1_28-2104_10154_10331file refers to misbehavior report sent at t= 28.2104 seconds sent by vehicle with pseudonym ID 10154, reporting the vehicle with pseudonym ID 10331 for misbehavior. Pseudonym is a temporary certificate that vehicle uses as ID, and mapping from real IDs to pseudonyms are avaiable in all logs.
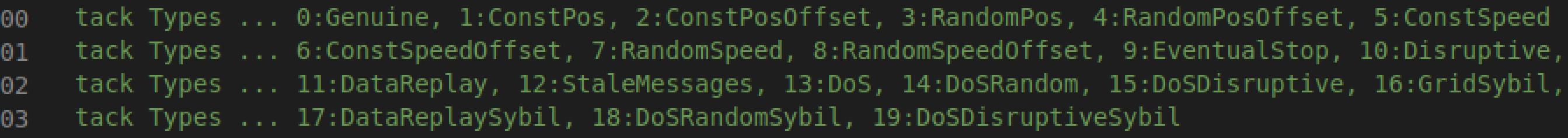
The attack types are given in omnetpp.ini file, as below:
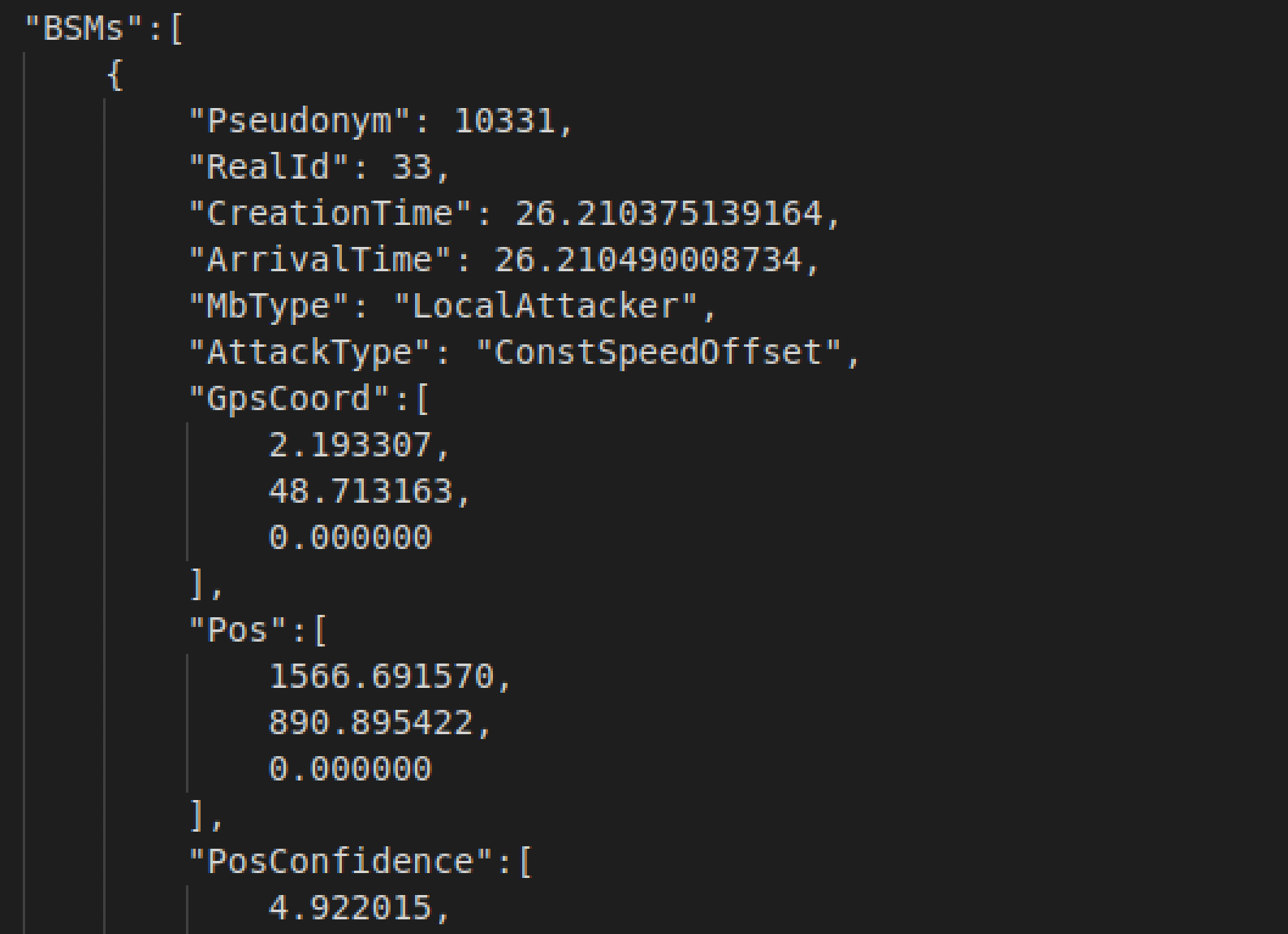
MDBSM_V1_10452) has the following record structure, with keys as BSMPrint:
-
Metadata: Credentials for the set of received messages. Here, the receiver has ID:45, pseudonym:10452, is an attacker itself (hard way to extract labels), and thisBSMPrintincludes messages received at t=26.21 seconds.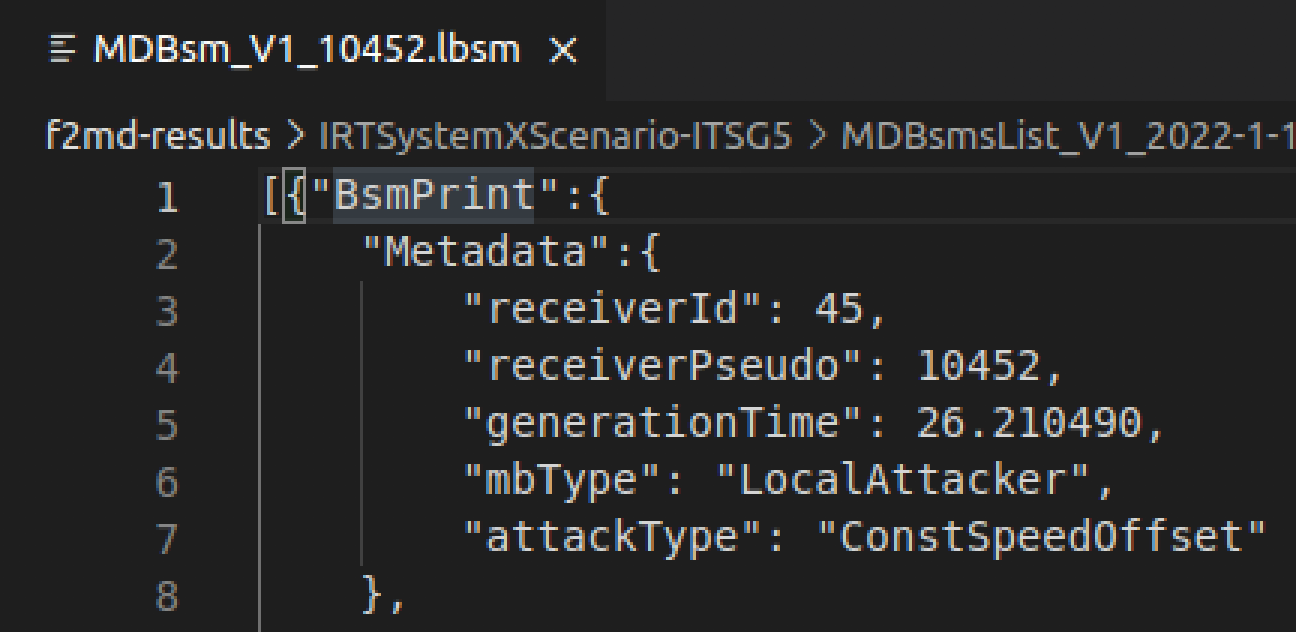
-
BSMCheck: Plausibility of self messages, we will not use this information for now. But essentially, some plausibility checks have low scores for vehicles that are attackers itself, which allow for detection. -
BSMs: List of received BSMs sent by other vehicles. Each BSM has following fields:- Pseudonym& Real ID: Credentials of message sender. The real ID here matches the extracted labels from Part 3.
- MbType: "LocalAttacker" if the sender is an attacker.
- AttackType: "$ATTACKNAME$", type of the attack if the sender is an attacker.
-
For each file and each BSM under BSMs list of
MDReport_V1_.., explained in Section 2-c, check if the sender is marked as an attacker or genuine for each message. Compare these reports for each BSM with the ground truth labels from Part 3 (vehicle-based labels), and Part 4-c (BSM-based labels). Create a confusion matrix with the number of True positive, True Negative, False Positive and False Negative reports. For more information on confusion matrix, refer to scikit-learn:confusion_matrix.
| Attack Type | True Positive | False Positive | False Negative |
| A5 (Constant Speed) | #TP-A5 (X%) | #FP-A5 (X%) | #FN-A5 (X%) |
| A6 (Constant Speed Offset) | #TP-A6 (X%) | #FP-A6 (X%) | #FN-A6 (X%) |
| ... | ... | ... | ... |
| A15 (DosDisruptive) | #TP-A15 (X%) | #FP-A15 (X%) | #FN-A15 (X%) |
The attack types are given in omnetpp.ini file, as below:

-
Refer to the calculations at legacy checks (at directory below) that our thresholding app uses to check the if the message is an attack:
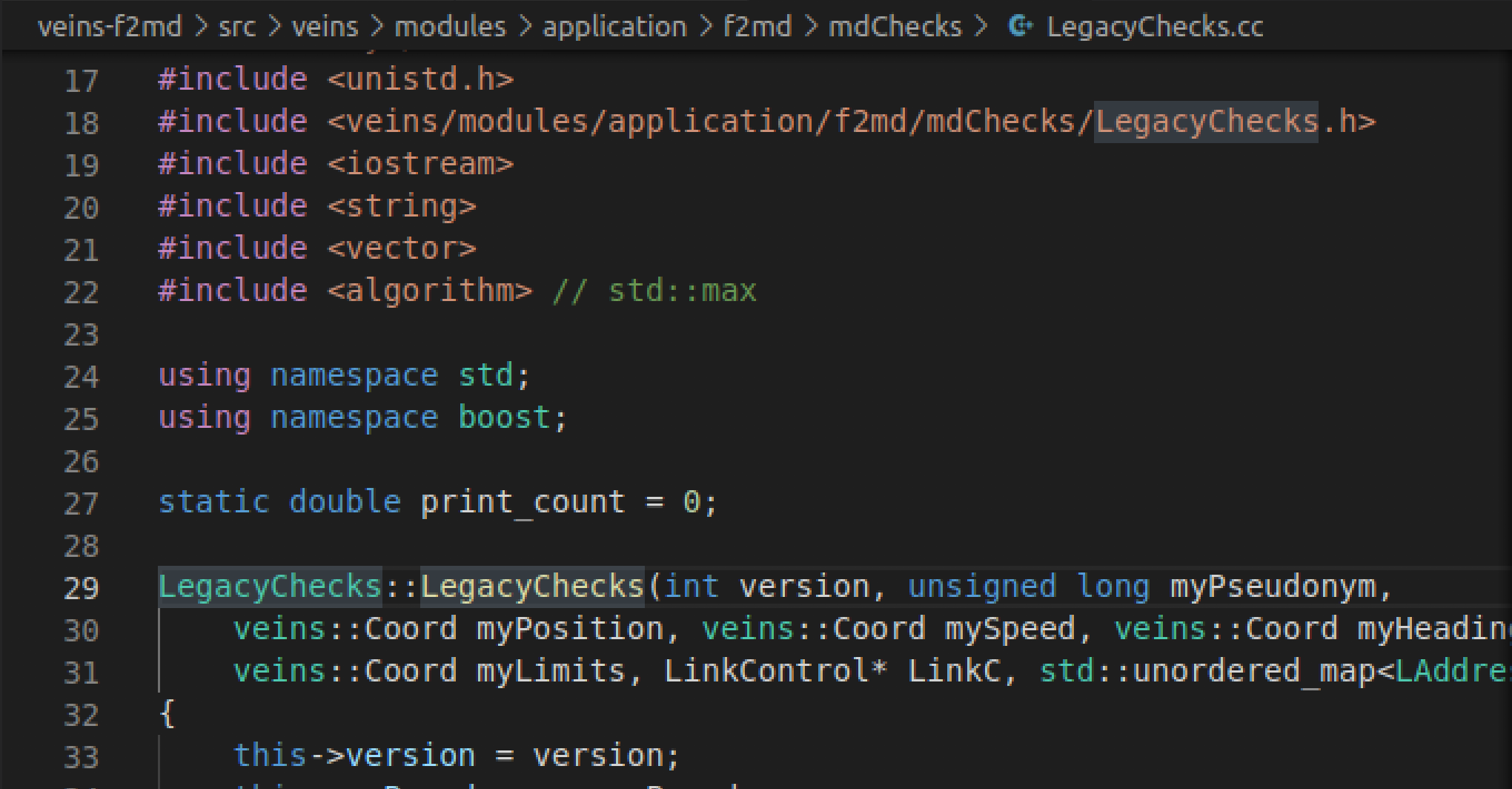 Briefly describe
Briefly describe PositionConsistancyCheck,SpeedConsistancyCheck, andPositionSpeedConsistancyCheckfunctions and list&comment on at least 3 attacks (from A5 through A15) that these checks can be useful. -
Briefly describe the thresholding app itself (at directory below), which uses the plausibility results (0 or 1) from legacy checks, compares it to a threshold and decides if message is attack or not.
What happens if we decrease the
Thresholdparameter that our thresholdApp uses, i.e. do we catch more attackers, do we get more false positives etc.?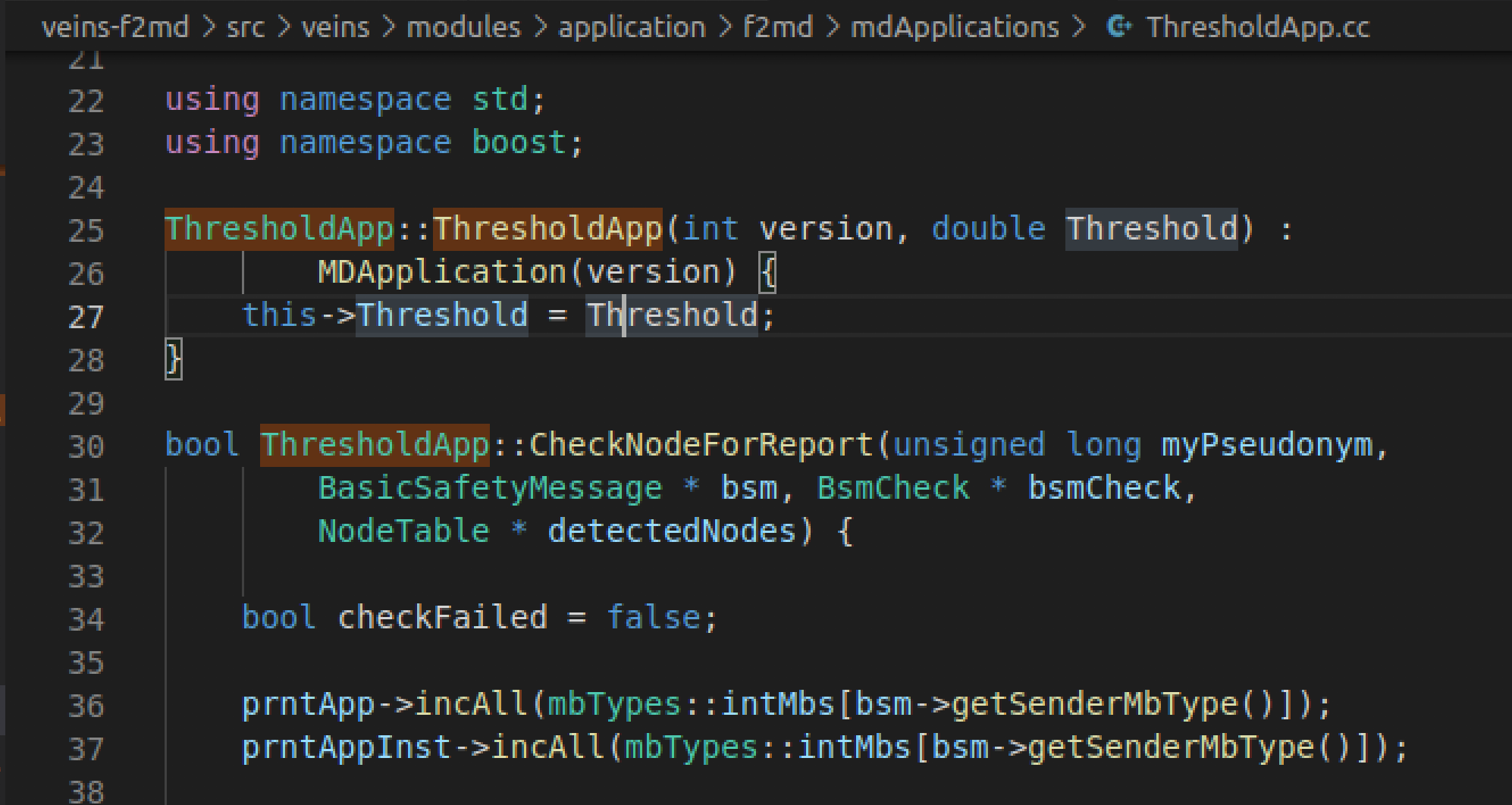
Submission Instructions
Save and submit your report as a PDF file of 2 pages or less. Your report should include the following:- A 2x2 confusion matrix of True Positive (TP), True Negative (TN), False Positive (FP), False Negative (FN): Confusion matrix of MBD performance from Part 4, including number of messages and percentages for each matrix entry. [5 pt]
- The attack based MBD performance table, as given in Part 5. [5 pt]
- Explanations of Legacy checks and thresholding app, as described in Part 6. [5 pt].
References
- https://veins.car2x.org/documentation/
- https://github.com/josephkamel/F2MD
- Here is another well-put VEINS tutorial for reference:
http://kjit.bme.hu/images/Tovabbi_allomanyok/Trafficlab/Research/SUMOTRACI/SUMO-VEINS_Tutorial.pdf - A custom simulation tutorial in VEINS:
http://cse.iitkgp.ac.in/~soumya/micro/t2-3.pdf - For the attack descriptions (A5-A15), refer to the original F2MD paper:
https://hal.archives-ouvertes.fr/hal-02527873/document