Secure Autonomous and Cyber-Physical Systems
Instructor: Prof. Sibin Mohan, Oregon State University
CS/ECE 599 | Winter 2022 Term | MW 2:00 - 3:50 PM PT | BAT 150
Paper Reading List
Administrivia
| Time per paper |
45 mins |
| Presentation Time |
30 mins |
| Discussion Time |
15 mins |
| Total Points |
30 [10/paper] |
Select one paper from each of the following groups: attacks, defenses, ethics & privacy.
Every speaker must present three papers in total, through the term.
Group A | Attacks
-
Eykholt, Kevin, et al. "Robust physical-world attacks on deep learning visual classification." Proceedings of the IEEE conference on computer vision and pattern recognition. 2018.
-
Jing, Pengfei, et al. "Too Good to Be Safe: Tricking Lane Detection in Autonomous Driving with Crafted Perturbations." 30th USENIX Security Symposium, 2021.
-
Patel, Naman et al. “Adaptive Adversarial Videos on Roadside Billboards: Dynamically Modifying Trajectories of Autonomous Vehicles.” 2019 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS) (2019): 5916-5921.
-
Sitawarin, C., Bhagoji, A. N., Mosenia, A., Chiang, M., & Mittal, P. (2018). "Darts: Deceiving autonomous cars with toxic sign". arXiv preprint arXiv:1802.06430.
-
Sathaye, Harshad, et al. "Wireless attacks on aircraft instrument landing systems." 28th USENIX Security Symposium 2019.
-
S. Jha et al., "ML-Based Fault Injection for Autonomous Vehicles: A Case for Bayesian Fault Injection," 2019 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), 2019, pp. 112-124, doi: 10.1109/DSN.2019.00025.
-
Liu, Songran, et al. "Leaking your engine speed by spectrum analysis of real-Time scheduling sequences." Journal of Systems Architecture 97 (2019): 455-466.
-
Yeom, Samuel et al. "Overfitting, Robustness, and Malicious Algorithms: A Study of Potential Causes of Privacy Risk in Machine Learning". Journal of Computer Security 28.1 (2020): 35-70.
-
Farha Jahan, Weiqing Sun, Quamar Niyaz, and Mansoor Alam. 2019. "Security Modeling of Autonomous Systems: A Survey". ACM Comput. Surv. 52, 5, Article 91 (September 2020), 34 pages. DOI:https://doi.org/10.1145/3337791
-
Wen, H., Zhao, Q., Chen, Q. A., & Lin, Z. "Automated cross-platform reverse engineering of CAN bus commands from mobile apps". In Proceedings 2020 Network and Distributed System Security Symposium (NDSS'20).
Group D | Defenses
-
Chuadhry Mujeeb Ahmed, Jianying Zhou, and Aditya P. Mathur. 2018. "Noise Matters: Using Sensor and Process Noise Fingerprint to Detect Stealthy Cyber Attacks and Authenticate sensors in CPS. In Proceedings of the 34th Annual Computer Security Applications Conference (ACSAC '18). 566–581. DOI:https://doi.org/10.1145/3274694.3274748
-
Roman A-S, Genge B, Duka A-V, Haller P. "Privacy-Preserving Tampering Detection in Automotive Systems" Electronics. 2021; 10(24):3161. https://doi.org/10.3390/electronics10243161
-
Lu, J., Sibai, H., Fabry, E., & Forsyth, D. "Standard detectors aren't (currently) fooled by physical adversarial stop signs". arXiv preprint arXiv:1710.03337.
-
Raj Gautam Dutta, Xiaolong Guo, Teng Zhang, Kevin Kwiat, Charles Kamhoua, Laurent Njilla, and Yier Jin. "Estimation of Safe Sensor Measurements of Autonomous System Under Attack". In Proceedings of the 54th Annual Design Automation Conference 2017 (DAC '17). https://doi.org/10.1145/3061639.3062241
-
Feth, P., Akram, M. N., Schuster, R., & Wasenmüller, O. "Dynamic risk assessment for vehicles of higher automation levels by deep learning". In International Conference on Computer Safety, Reliability, and Security (pp. 535-547). Springer.
-
A. Singandhupe and H. M. La, "MCC-EKF for Autonomous Car Security," 2020 Fourth IEEE International Conference on Robotic Computing (IRC), 2020, pp. 306-313, doi: 10.1109/IRC.2020.00056.
-
Abera, T., Bahmani, R., Brasser, F., Ibrahim, A., Sadeghi, A. R., & Schunter, M. "DIAT: Data Integrity Attestation for Resilient Collaboration of Autonomous Systems". In Proceedings 2020 Network and Distributed System Security Symposium (NDSS) 2019.
-
J. Kamel, A. Kaiser, I. ben Jemaa, P. Cincilla and P. Urien, "CaTch: A Confidence Range Tolerant Misbehavior Detection Approach," 2019 IEEE Wireless Communications and Networking Conference (WCNC), 2019, pp. 1-8, doi: 10.1109/WCNC.2019.8885740.
-
Yang, Y., & Huang, G. (2020). "Map-based localization under adversarial attacks". In Robotics Research (pp. 775-790). Springer
-
Q. Liu, Y. Mo, X. Mo, C. Lv, E. Mihankhah and D. Wang, "Secure Pose Estimation for Autonomous Vehicles under Cyber Attacks," 2019 IEEE Intelligent Vehicles Symposium (IV), 2019, pp. 1583-1588, doi: 10.1109/IVS.2019.8814161.
Group EP | Ethics & Privacy
-
Thierry Fraichard. "Will the Driver Seat Ever Be Empty?" [Research Report] RR-8493, INRIA. 2014. hal-00965176v2
-
Héder, M. "The epistemic opacity of autonomous systems and the ethical consequences". AI & Soc (2020). https://doi.org/10.1007/s00146-020-01024-9
-
Berendt, Bettina. 2020. “(De)constructing Ethics for Autonomous Cars: A Case Study of Ethics Pen-Testing towards ‘AI for the Common Good’”. The International Review of Information Ethics 28 (June). Edmonton, Canada. https://doi.org/10.29173/irie381.
-
T. Holstein and G. Dodig-Crnkovic, "Avoiding the Intrinsic Unfairness of the Trolley Problem" 2018 IEEE/ACM International Workshop on Software Fairness (FairWare), 2018, pp. 32-37, doi: 10.23919/FAIRWARE.2018.8452918.
-
Kulicki, Piotr & Trypuz, Robert & Musielewicz, Michael. "Kulicki, Piotr & Trypuz, Robert & Musielewicz, Michael. (2018). Towards a Formal Ethics for Autonomous Cars", Deontic Logic and Normative Systems. 14th International Conference, DEON 2018.
-
Glancy, Dorothy J. "Privacy in autonomous vehicles," Santa Clara L. Rev. 52 (2012): 1171.
-
J. Wang, Z. Cai and J. Yu, "Achieving Personalized $k$-Anonymity-Based Content Privacy for Autonomous Vehicles in CPS," in IEEE Transactions on Industrial Informatics, vol. 16, no. 6, pp. 4242-4251, June 2020, doi: 10.1109/TII.2019.2950057.
-
S. Karnouskos and F. Kerschbaum, "Privacy and Integrity Considerations in Hyperconnected Autonomous Vehicles," in Proceedings of the IEEE, vol. 106, no. 1, pp. 160-170, Jan. 2018, doi: 10.1109/JPROC.2017.2725339.
-
Zhang, Heng, et al. "Privacy and performance trade-off in cyber-physical systems." IEEE Network 30.2 (2016): 62-66.
-
M. Keshk, E. Sitnikova, N. Moustafa, J. Hu and I. Khalil, "An Integrated Framework for Privacy-Preserving Based Anomaly Detection for Cyber-Physical Systems," in IEEE Transactions on Sustainable Computing, vol. 6, no. 1, pp. 66-79, 1 Jan.-March 2021, doi: 10.1109/TSUSC.2019.2906657.
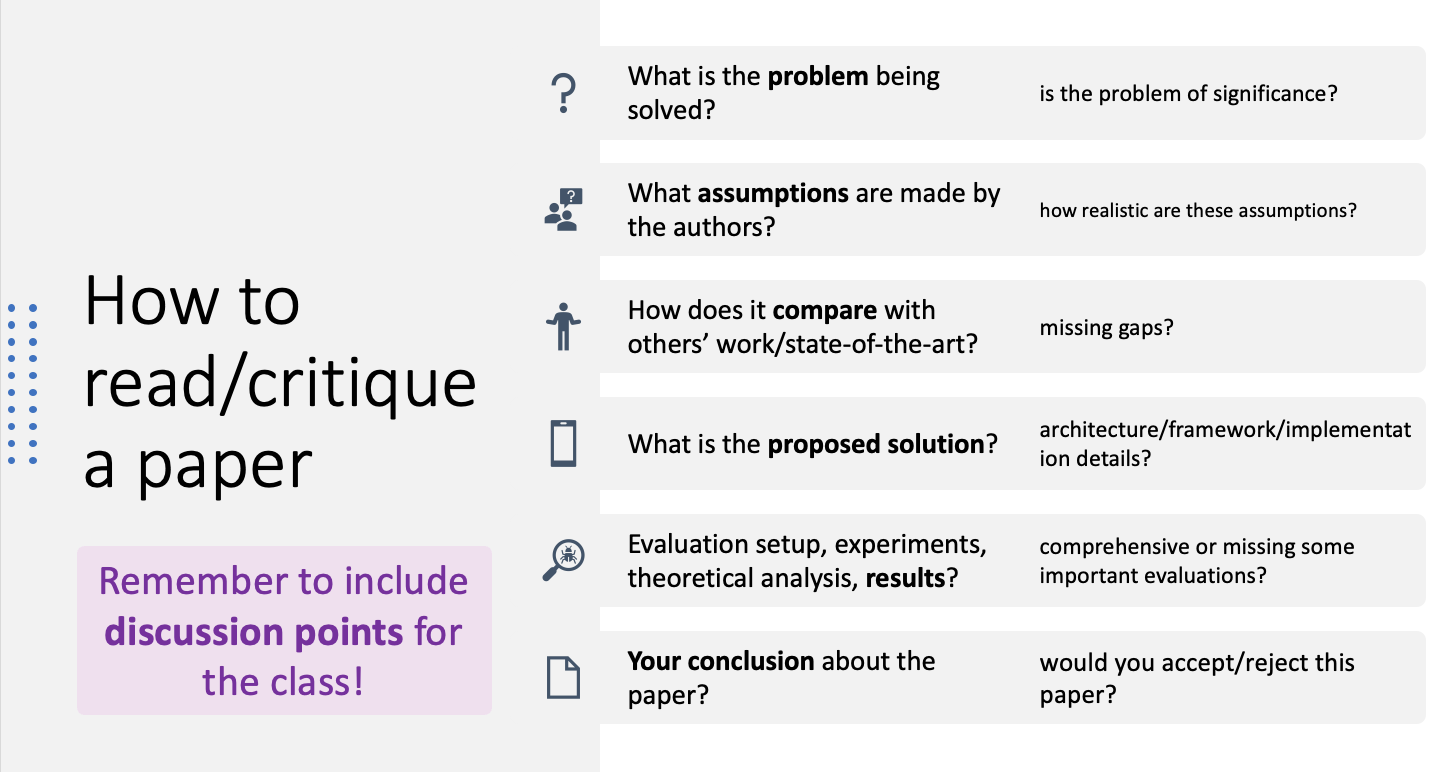
How to Critique a Paper