Secure Autonomous and Cyber-Physical Systems
Instructor: Prof. Sibin Mohan, Oregon State University
CS/ECE 599 | Winter 2022 Term | MW 2:00 - 3:50 PM PT | BAT 150
MP II-B: Middleware Security [Extra Credit]
Administrivia
| Announcement Date |
Feb. 28, 2022 |
| Submission Date |
Mar. 07, 2022 |
| Submission Time |
11:59PM PT |
| Total Points |
10 |
Objective
Middleware is often used to exchange messages between modules/components of autonomous systems.
In part A, we explored how PX4 module uses uORB to subscribe to topics.
For this MP, we will focus on Man-In-The-Middle attacks.
-
Create custom uORB messages.
-
Perform Man-In-The-Middle (MitM) attacks.
Prelude
Middleware, also called Data Distribution Service (DDS), is an integral part in autonomous vehicles.
The middleware we have explored is uORB which is used by PX4 autopilot.
There also exists Ardupilot, another autopilot software, which uses Robotic Operating System (ROS) as middleware.
uORB is similar to the original ROS since they follow the publish/subscribe paradigm.
Because application of these middleswares are safety-critical in nature, there are some security concerns since both were not initially designed with security in mind.
ROS2, a newer standard of ROS with major changes, which was released (late 2010s) follows a DDS security specification
The specification allows authentication, authorization, and encryption.
Therefore, in this MP, we will investigate why such security measures are necessary by performing MitM by hijacking a uORB topic.
We assume the adversary (you) can deploy its malicious module into PX4 and can slightly change particular module of the firmware(specifically the EKF module).
Running the PX4-SITL
This MP has an extra step where you have to run a server script.
There are additional files which you must download from here which contains the mp2_server.py and mp2_lib.
Later instructional steps will describe where to correctly extract the additional files.
Running the simulator
-
Start with the MP2 base directory:
cd /home/student/Desktop/MP2
-
Run the MP2 server:
python3 mp2_server.py which should wait for the mp2 module in the PX4 to run

-
In another terminal, change the directoy to
cd /home/student/Desktop/MP2/PX4-Autopilot
-
Compile and start the simulation by running:
make px4_sitl gazebo
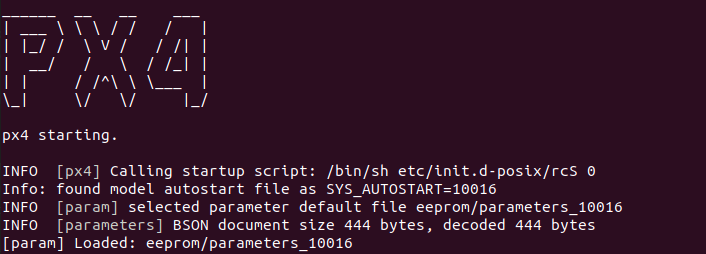
-
In PX4 command prompt, start the mp2 module
mp2 start

-
In the third terminal, change the directory to the MP2 base directory and run the offboard control:
python3 mp2_offboard_control.py
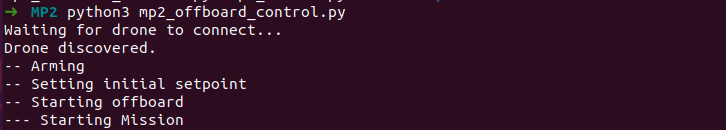
Man-In-The-Middle
-
We will hijack a topic by creating a custom uORB topic and causing the EKF module to publish to the malicious topic than the true topic.
-
EKF module will be publishing under a malicious uORB topic.
-
MP2 module will subscribe to the malicious topic and publish under the true topic with spoofed values.
-
We will look into four types of spoofing: constant offset, random offset, rotated, and scaled.
-
Create a custom message that has the same structure as the
vehicle_local_position under a different name.
- Go to the
msg in PX4-Autopilot directory
- Copy the
vehicle_local_position.msg under a different name of your choosing.
- We will refer to it as
vehicle_local_position_copy
-
At the bottom of the
vehicle_local_position.msg, there should be two commented out lines
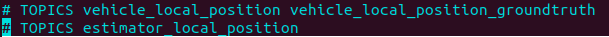
-
The commented out lines are responsible for it will be declared in
#inlcude.
-
Therefore, modify
vehicle_local_position_copy.msg to make it distict from the original.
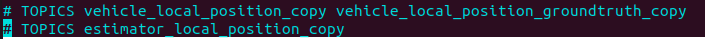
-
Modify the
msg/CMakeLists.txt by adding vehicle_local_position_copy.msg to set(msg_files).
-
Hijack the
vehicle_local_position topic.
-
We want to modify the EKF module so that it publishes under the malicious topic.
-
In side
PX4-Autopilot/src/modules/ekf2/ we need to modify the EKF2Selector.cpp and EKF2Selector.hpp.
-
In side
EKF2Selector.hpp, first include the new message #include <uORB/topics/vehicle_local_position_copy.h>
-
Then find the line
uORB::Publication<vehicle_local_position_s> _vehicle_local_position_pub{ORB_ID(vehicle_local_position)}; which is responsible for publishing the topic.
-
Replace it with
uORB::Publication<vehicle_local_position_copy_s> _vehicle_local_position_pub{ORB_ID(vehicle_local_position_copy)}; to make the variable publish under different topic.
-
Go to the
EKF2Selector.cpp and find the function PublishVehicleLocalPosition().
-
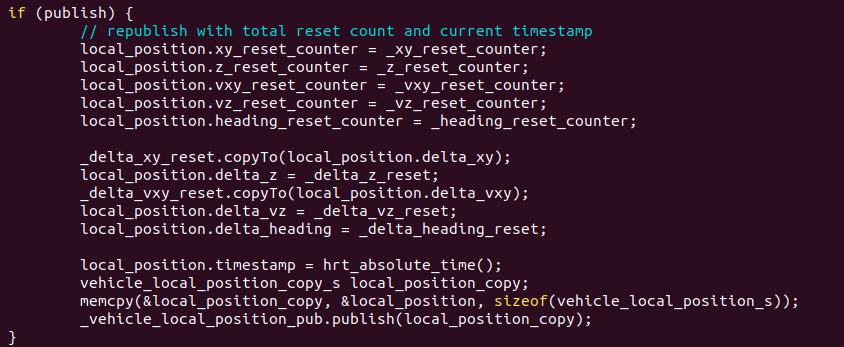
In the very last few lines of code, find the line where
_vehicle_local_position_pub is used, create a struct of the new malicious and copy the vehicle_local_position struct to it using memcpy()
-
Should look like this:
-
Make the mp2 module communicate with the
mp2_server.py.
-
Download the additional files here which contains
mp2_server.py and mp2_lib.cpp and mp2_lib.h
-
Extract the
mp2_server.py in the ~/Desktop/MP2/ directory.
-
Extract the
mp2_lib.cpp and mp2_lib.h in the ~/Desktop/MP2/PX4-Autopilot/src/modules/mp2 directory.
-
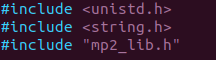
Modify the
mp2.hpp inside the modules/mp2
-
Include the
mp2_lib.h in mp2.hpp
-
Add the following line
Mp2Server * mp2server; to the private section of the MP2 class.
-
Add
mp2_lib.cpp and mp2_lib.h in CMakeLists.txt under SRC
-
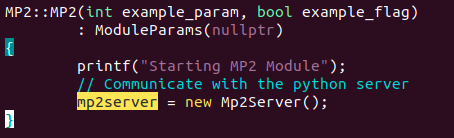
Modify the
mp2.cpp inside the modules/mp2 to read the new topic.
-
Initizlize the
mp2server in the MP2contructor
-
Subscribe to
vehicle_local_position_copy instead of vehicle_local_position (refer to MP2 part A, remember to change the struct type as well).
-
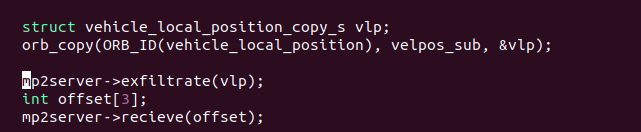
Inside the
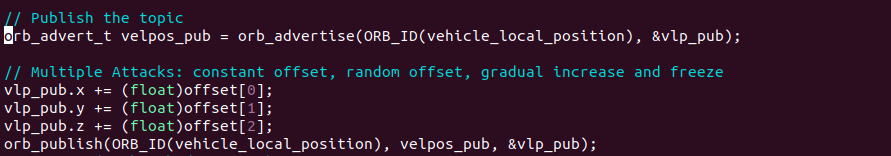
run() function, use mp2server.exfiltrate() to send the subscribed data to the server and mp2server.recieve() to get the offset values back from the server.
-
Create
vehicle_local_position struct and memcpy() the subscribed data to the struct.
-
Add the values recieved from the server to the x, y, z position of the struct.
-
Create publishing id (similar to how there was subscribe id in part A) using
orb_advertise()
-
Publish the topic using
orb_publish()
-
Implement the attack types in the
mp2_server.py
-
Find the "TODO:" flags in the script and implement the corresponding attack.
-
Fixed offset attack adds fixed constant value (of your choosing) to each of the position values (specify the value you used in the report).
-
Random offset attack adds random value in a specified range (of your choosing) to each of the position values (specify the range of values you used in the report).
-
Flipped attack causes move in a trajectory where the X and Y positions are flipped.
-
Scaled attack causes move in a trajectory where the X and Y movements are scaled by a constant (i.e., if the mission is for the vehicle to move along x axis by 2 meters, in actualality it would move by 2*constant).
-
The
mp2_server.py outputs exfil_traj.npy which can be used by the prior plotting script by finding changing the "traj.npy" to "exfil_traj.npy".
Note: for each of the above missions, repeat them for the missions from MP II-A, i.e. linear and circular.
Also, the "mission" is finite time and only should attack between the interval where drone takes off and stop when it lands.
Submission Instructions
-
Man-In-The-Middle implementation (fixed offset, random offset, flipped, and scaled) description [2 points]
-
Plot of the missions with MitM implementations: two missions (linear and circular) on the four attack types [8 points]










